

Protection as you've never experienced
We don’t just ensure that we comply with GDPR and other privacy laws, we help our customers meet the requirements too. By using YEO for your business communications, you can rest assured that all data is encrypted and all users are verified.
Identity-First Security
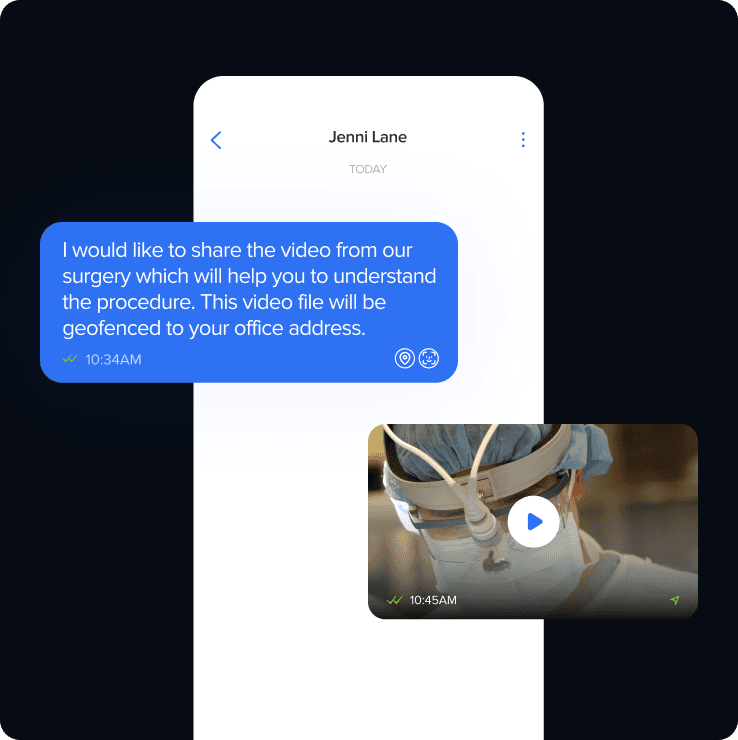
YEO for Business goes beyond traditional messaging by using patented continuous facial recognition to authenticate users, ensuring a secure network where every user is identified. This prevents phishing, fraud, and unauthorized access, protecting messages from cyber attacks and compromised devices while maintaining security and confidentiality.
Identity-First Security
YEO for Business goes beyond traditional messaging by using patented continuous facial recognition to authenticate users, ensuring a secure network where every user is identified. This prevents phishing, fraud, and unauthorized access, protecting messages from cyber attacks and compromised devices while maintaining security and confidentiality.

Identity-First Security
YEO for Business goes beyond traditional messaging by using patented continuous facial recognition to authenticate users, ensuring a secure network where every user is identified. This prevents phishing, fraud, and unauthorized access, protecting messages from cyber attacks and compromised devices while maintaining security and confidentiality.

End-to-End Encryption
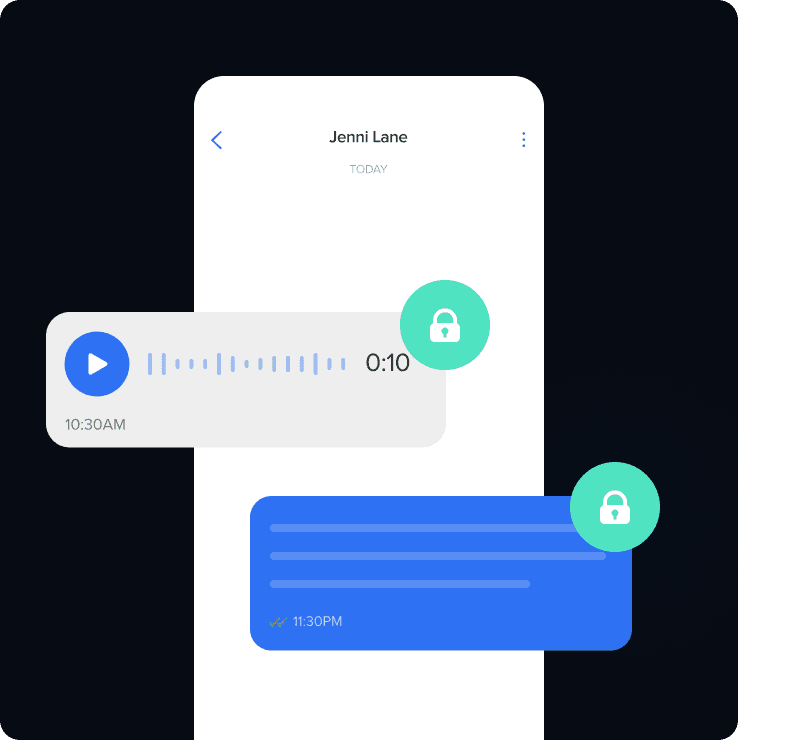
All messages and data remains fully encrypted during transit and at rest eliminating the need for complex security policies of VPN tunnelling. Using double ratchet encryption means that every message has a unique key ensuring the highest security at all times.
End-to-End Encryption
All messages and data remains fully encrypted during transit and at rest eliminating the need for complex security policies of VPN tunnelling. Using double ratchet encryption means that every message has a unique key ensuring the highest security at all times.

End-to-End Encryption
All messages and data remains fully encrypted during transit and at rest eliminating the need for complex security policies of VPN tunnelling. Using double ratchet encryption means that every message has a unique key ensuring the highest security at all times.

Remote Access Control
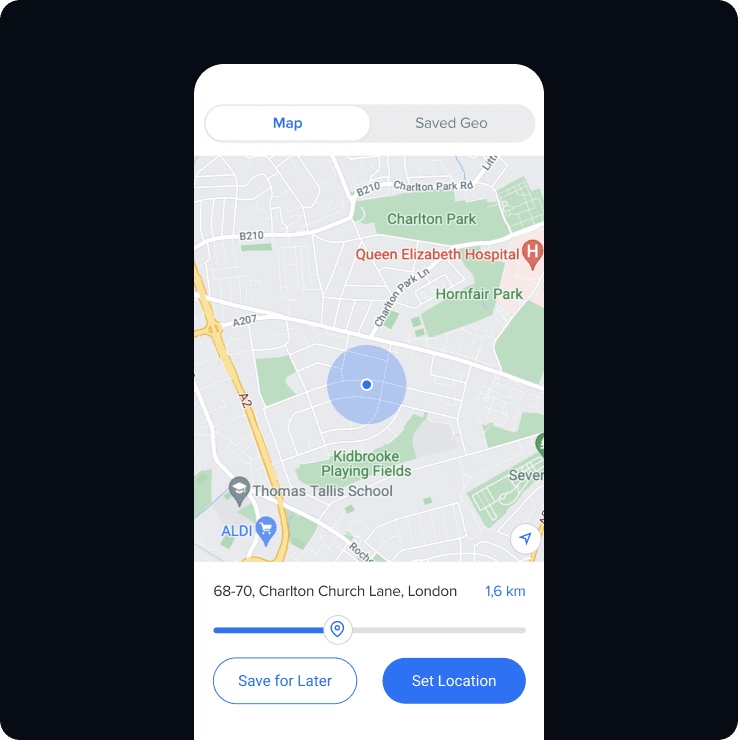
User management through an interactive management console enables instant access revocation when employees leave, or devices are lost or stolen. YEO enables engagement policies to be initiated at individual, group or company level ensuring control and security of information flow at all times.
Remote Access Control
User management through an interactive management console enables instant access revocation when employees leave, or devices are lost or stolen. YEO enables engagement policies to be initiated at individual, group or company level ensuring control and security of information flow at all times.

Remote Access Control
User management through an interactive management console enables instant access revocation when employees leave, or devices are lost or stolen. YEO enables engagement policies to be initiated at individual, group or company level ensuring control and security of information flow at all times.



Security
Whitepaper
In the YEO security whitepaper we go into more detail about our security and privacy practices throughout the YEO Messaging Individual Application.


Security
Whitepaper
In the YEO security whitepaper we go into more detail about our security and privacy practices throughout the YEO Messaging Individual Application.


Security
Whitepaper
In the YEO security whitepaper we go into more detail about our security and privacy practices throughout the YEO Messaging Individual Application.


Cryptography
Whitepaper
This document describes the encryption model used in YEO Messaging Application to securely exchange messages between users.


Cryptography
Whitepaper
This document describes the encryption model used in YEO Messaging Application to securely exchange messages between users.


Cryptography
Whitepaper
This document describes the encryption model used in YEO Messaging Application to securely exchange messages between users.
Advanced admin controls for ultimate security
Take full control of your organisation’s communications with powerful admin features.
Compliance & Auditing
Perform audits with searchable records on users and content to ensure compliance.
Compliance & Auditing
Perform audits with searchable records on users and content to ensure compliance.
Compliance & Auditing
Perform audits with searchable records on users and content to ensure compliance.
Invite-Only Access
Maintain security with a closed platform, where only approved users can join.
Invite-Only Access
Maintain security with a closed platform, where only approved users can join.
Invite-Only Access
Maintain security with a closed platform, where only approved users can join.
Centralised User Management
Admins have full control over user access and permissions within their company.
Centralised User Management
Admins have full control over user access and permissions within their company.
Centralised User Management
Admins have full control over user access and permissions within their company.
